Encryption Policy Template
Document content
This encryption policy template has 3 pages and is a MS Word file type listed under our human resources documents.
Sample of our encryption policy template:
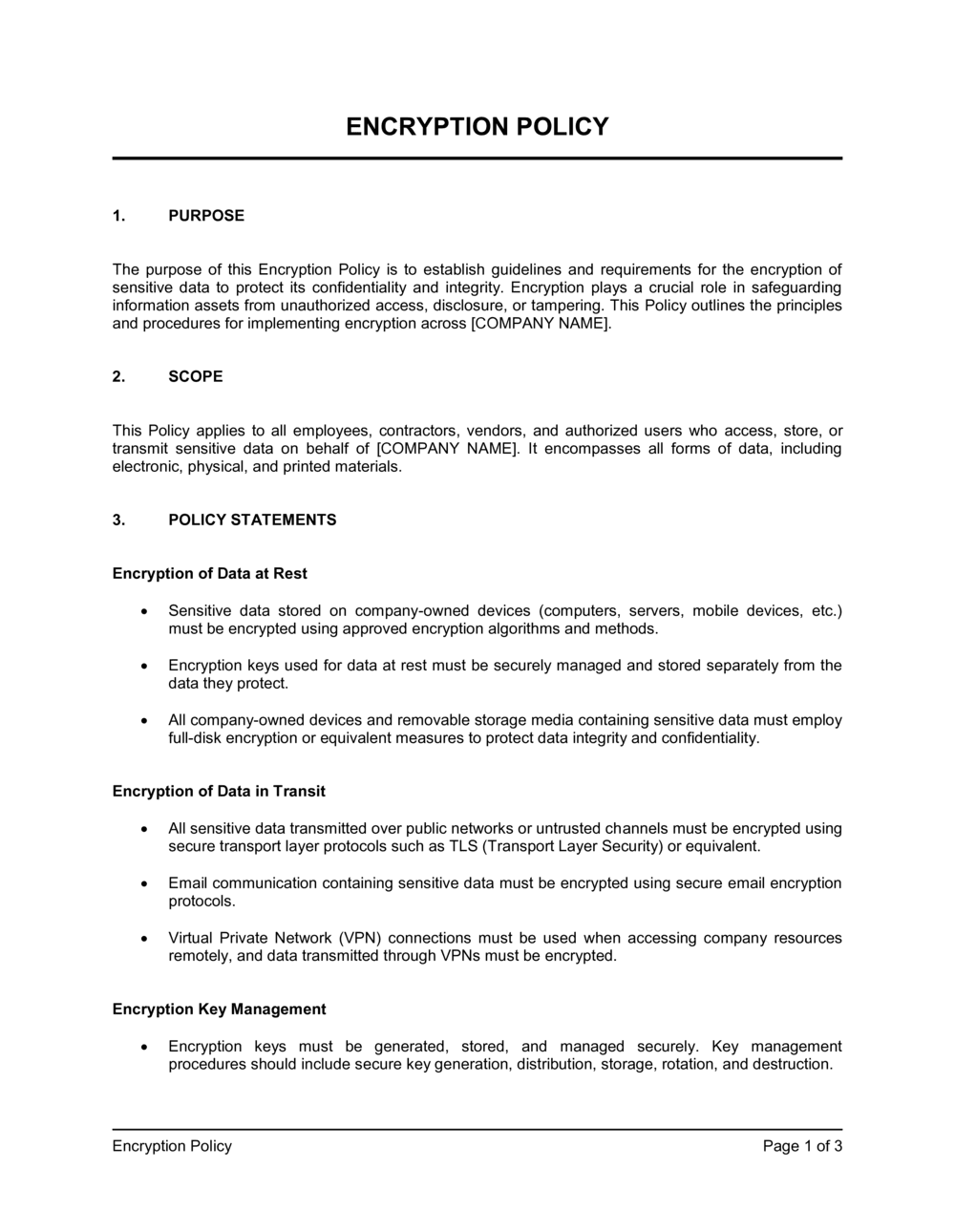
ENCRYPTION POLICY PURPOSE The purpose of this Encryption Policy is to establish guidelines and requirements for the encryption of sensitive data to protect its confidentiality and integrity. Encryption plays a crucial role in safeguarding information assets from unauthorized access, disclosure, or tampering. This Policy outlines the principles and procedures for implementing encryption across [COMPANY NAME]. SCOPE This Policy applies to all employees, contractors, vendors, and authorized users who access, store, or transmit sensitive data on behalf of [COMPANY NAME]. It encompasses all forms of data, including electronic, physical, and printed materials. POLICY STATEMENTS Encryption of Data at Rest Sensitive data stored on company-owned devices (computers, servers, mobile devices, etc.) must be encrypted using approved encryption algorithms and methods. Encryption keys used for data at rest must be securely managed and stored separately from the data they protect. All company-owned devices and removable storage media containing sensitive data must employ full-disk encryption or equivalent measures to protect data integrity and confidentiality. Encryption of Data in Transit All sensitive data transmitted over public networks or untrusted channels must be encrypted using secure transport layer protocols such as TLS (Transport Layer Security) or equivalent. Email communication containing sensitive data must be encrypted using secure email encryption protocols. Virtual Private Network (VPN) connections must be used when accessing company resources remotely, and data transmitted through VPNs must be encrypted. Encryption Key Management Encryption keys must be generated, stored, and managed securely. Key management procedures should include secure key generation, distribution, storage, rotation, and destruction. Access to encryption keys must be restricted to authorized personnel only, and access logs should be maintained. Lost or compromised encryption keys must be reported immediately to the designated security personnel. Compliance and Monitoring Regular Audits and Assessments: To ensure the ongoing effectiveness of our Encryption Policy and the protection of sensitive data, [COMPANY NAME] is committed to conducting regular audits and assessments. These evaluations will encompass the following key aspects: Technical Audits: Our IT security team will perform technical audits of encryption implementation across company devices, networks, and data storage systems. These audits will include assessments of encryption algorithms, key management practices, and adherence to encryption standards.
Reviewed on

Document content
This encryption policy template has 3 pages and is a MS Word file type listed under our human resources documents.
Sample of our encryption policy template:
ENCRYPTION POLICY PURPOSE The purpose of this Encryption Policy is to establish guidelines and requirements for the encryption of sensitive data to protect its confidentiality and integrity. Encryption plays a crucial role in safeguarding information assets from unauthorized access, disclosure, or tampering. This Policy outlines the principles and procedures for implementing encryption across [COMPANY NAME]. SCOPE This Policy applies to all employees, contractors, vendors, and authorized users who access, store, or transmit sensitive data on behalf of [COMPANY NAME]. It encompasses all forms of data, including electronic, physical, and printed materials. POLICY STATEMENTS Encryption of Data at Rest Sensitive data stored on company-owned devices (computers, servers, mobile devices, etc.) must be encrypted using approved encryption algorithms and methods. Encryption keys used for data at rest must be securely managed and stored separately from the data they protect. All company-owned devices and removable storage media containing sensitive data must employ full-disk encryption or equivalent measures to protect data integrity and confidentiality. Encryption of Data in Transit All sensitive data transmitted over public networks or untrusted channels must be encrypted using secure transport layer protocols such as TLS (Transport Layer Security) or equivalent. Email communication containing sensitive data must be encrypted using secure email encryption protocols. Virtual Private Network (VPN) connections must be used when accessing company resources remotely, and data transmitted through VPNs must be encrypted. Encryption Key Management Encryption keys must be generated, stored, and managed securely. Key management procedures should include secure key generation, distribution, storage, rotation, and destruction. Access to encryption keys must be restricted to authorized personnel only, and access logs should be maintained. Lost or compromised encryption keys must be reported immediately to the designated security personnel. Compliance and Monitoring Regular Audits and Assessments: To ensure the ongoing effectiveness of our Encryption Policy and the protection of sensitive data, [COMPANY NAME] is committed to conducting regular audits and assessments. These evaluations will encompass the following key aspects: Technical Audits: Our IT security team will perform technical audits of encryption implementation across company devices, networks, and data storage systems. These audits will include assessments of encryption algorithms, key management practices, and adherence to encryption standards.
Easily Create Any Business Document You Need in Minutes.
Download or open template
Access over 3,000+ business and legal templates for any business task, project or initiative.
Edit and fill in the blanks
Customize your ready-made business document template and save it in the cloud.
Save, Share, Export, or Sign
Share your files and folders with your team. Create a space of seamless collaboration.


