Data Management Policy Template

Document content
This data management policy template has 5 pages and is a MS Word file type listed under our finance & accounting documents.
Sample of our data management policy template:
DATA MANAGEMENT POLICY PURPOSE The purpose of this Data Management Policy at [COMPANY NAME] is to establish a framework for managing data within the organization. This Policy ensures that all data is handled responsibly, securely, and in alignment with the company's strategic objectives and regulatory requirements. It aims to foster data integrity, security, and quality. RESEARCH DEVELOPMENT Responsibility Chief Data Officer (CDO): The CDO is the primary authority overseeing the entire data management process. This role includes setting strategic data directions, ensuring alignment with the company's overall goals, and maintaining high standards of data integrity and quality. The CDO also plays a critical role in resource allocation, risk management, and overseeing the ethical conduct of data activities. Data Stewards: These individuals bear the responsibility for the hands-on management of data. Their duties encompass initiating new data management protocols, diligently planning data activities, and ensuring the smooth execution of data-related tasks in accordance with this Policy. They must also maintain open lines of communication with the CDO, stakeholders, and their teams, ensuring that all parties are informed and engaged throughout the data management process. Data Classification Data Categorization: Data should be classified into categories such as public, internal, confidential, and restricted. Each category has specific handling and access protocols to ensure proper data management. Sensitivity and Criticality Assessment: Data should be assessed for sensitivity and criticality to determine the appropriate security and privacy measures. Data Quality Accuracy: Ensure that data is accurate and free from errors. Consistency: Maintain data consistency across different systems and databases. Completeness: Ensure that all required data is complete and nothing essential is missing. Timeliness: Data should be up-to-date and available when needed. DATA SECURITY Access Control Role-Based Access: Access to data should be granted based on the roles and responsibilities of employees. Authentication and Authorization: Implement strong authentication and authorization mechanisms to ensure that only authorized individuals have access to sensitive data. Data Encryption At Rest: Data should be encrypted when stored in databases or on physical media. In Transit: Data should be encrypted when transmitted over networks to protect it from interception. Incident Response Breach Notification: Establish protocols for notifying affected parties in the event of a data breach. Mitigation Measures: Develop and implement measures to mitigate the effects of a data breach and prevent future incidents. DATA PRIVACY Compliance with Laws Regulatory Requirements: Ensure compliance with relevant data protection laws and regulations, such as GDPR, CCPA, and HIPAA. Privacy by Design: Incorporate privacy considerations into the design and development of systems and processes. Data Subject Rights
Reviewed on

Document content
This data management policy template has 5 pages and is a MS Word file type listed under our finance & accounting documents.
Sample of our data management policy template:
DATA MANAGEMENT POLICY PURPOSE The purpose of this Data Management Policy at [COMPANY NAME] is to establish a framework for managing data within the organization. This Policy ensures that all data is handled responsibly, securely, and in alignment with the company's strategic objectives and regulatory requirements. It aims to foster data integrity, security, and quality. RESEARCH DEVELOPMENT Responsibility Chief Data Officer (CDO): The CDO is the primary authority overseeing the entire data management process. This role includes setting strategic data directions, ensuring alignment with the company's overall goals, and maintaining high standards of data integrity and quality. The CDO also plays a critical role in resource allocation, risk management, and overseeing the ethical conduct of data activities. Data Stewards: These individuals bear the responsibility for the hands-on management of data. Their duties encompass initiating new data management protocols, diligently planning data activities, and ensuring the smooth execution of data-related tasks in accordance with this Policy. They must also maintain open lines of communication with the CDO, stakeholders, and their teams, ensuring that all parties are informed and engaged throughout the data management process. Data Classification Data Categorization: Data should be classified into categories such as public, internal, confidential, and restricted. Each category has specific handling and access protocols to ensure proper data management. Sensitivity and Criticality Assessment: Data should be assessed for sensitivity and criticality to determine the appropriate security and privacy measures. Data Quality Accuracy: Ensure that data is accurate and free from errors. Consistency: Maintain data consistency across different systems and databases. Completeness: Ensure that all required data is complete and nothing essential is missing. Timeliness: Data should be up-to-date and available when needed. DATA SECURITY Access Control Role-Based Access: Access to data should be granted based on the roles and responsibilities of employees. Authentication and Authorization: Implement strong authentication and authorization mechanisms to ensure that only authorized individuals have access to sensitive data. Data Encryption At Rest: Data should be encrypted when stored in databases or on physical media. In Transit: Data should be encrypted when transmitted over networks to protect it from interception. Incident Response Breach Notification: Establish protocols for notifying affected parties in the event of a data breach. Mitigation Measures: Develop and implement measures to mitigate the effects of a data breach and prevent future incidents. DATA PRIVACY Compliance with Laws Regulatory Requirements: Ensure compliance with relevant data protection laws and regulations, such as GDPR, CCPA, and HIPAA. Privacy by Design: Incorporate privacy considerations into the design and development of systems and processes. Data Subject Rights
Easily Create Any Business Document You Need in Minutes.
Download or open template
Access over 3,000+ business and legal templates for any business task, project or initiative.
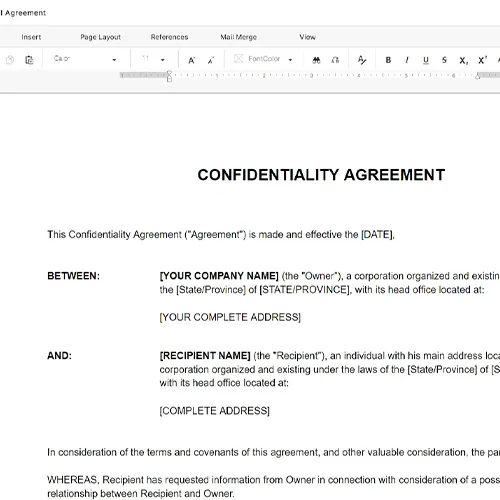
Edit and fill in the blanks
Customize your ready-made business document template and save it in the cloud.
Save, Share, Export, or Sign
Share your files and folders with your team. Create a space of seamless collaboration.


